Inline DDoS Mitigation Filters Using XDP and Custom Logic
Inline DDoS Mitigation Filters Using XDP and Custom Logic
Modern DDoS attacks are no longer simple volumetric floods. They're sophisticated, persistent, and tailored to exploit the weak points of specific applications. At CubePath, we’ve engineered a fully inline, ultra-low-latency mitigation stack based on XDP, eBPF, and Mellanox hardware acceleration, capable of defending complex environments in real time.
Whether it’s a high frequency API, a remote desktop platform, or a multiplayer game server, our system filters malicious traffic at the edge with full control, speed, and precision.
Why We Use XDP + eBPF
At the core of our system is XDP (eXpress Data Path) a high performance packet processing layer built into the Linux kernel. Using eBPF, we can load small programs that inspect and act on packets with minimal overhead.
This allows us to:
- Block or rate limit traffic before it reaches the networking stack
- Apply advanced logic without context switching to user space
- Deploy inline filtering at 10G–100G line rate, with near-zero latency
By combining XDP with our own detection and control layers, we can respond instantly to threats without introducing friction to clean traffic.
Symmetric TCP Validation
One of our core techniques is symmetric TCP validation, which ensures that packets follow a valid handshake process.
✅ Legitimate connections are confirmed bidirectionally
❌ Spoofed SYNs or malformed TCP flows are dropped immediately
This prevents a wide range of spoofing and exhaustion attacks at the packet level particularly relevant for services like RDP, web backends, and gaming protocols.
Application-Aware Mitigation Profiles
We maintain a set of custom mitigation profiles designed to align with the behavior of real world applications.
These profiles allow us to apply filtering strategies that are aware of the underlying protocol characteristics, traffic patterns, and performance requirements helping to reduce false positives while maintaining strong protection.
Whether it's latency sensitive services, gaming platforms, remote access tools, or HTTP(S) APIs, our system is optimized to apply the right level of mitigation for each case without compromising user experience.
Payload-Based Filtering & Static Rules
We go far beyond traditional port/IP firewalls. Our inline engine supports:
- Payload inspection at key offsets
- Header validation across TCP, UDP, and higher layer protocols
- Rate limiting by endpoint, ASN, or region
- TCP flag tracking and session consistency checks
This enables us to block malformed HTTP(S) floods, brute force RDP attempts, and protocol violations in real time without relying on deep packet decryption or external scrubbing.
Hardware Offloading with Mellanox ConnectX-6
To ensure scalability under attack, we use Mellanox ConnectX-6 SmartNICs, allowing us to offload:
- Flow steering and early packet drop logic
- Segmentation and checksum tasks
- Rate limiting at the NIC level
This helps us maintain performance at 10/25/40/100Gbps even during sustained and complex attack scenarios.
Our Custom Detection Engine
Mitigation is only effective when it’s triggered precisely. That’s why we’ve developed a detection layer that analyzes:
- Traffic patterns and anomalies over time
- Irregular protocol behavior and connection patterns
- ASN and geo level fluctuations
- Indicators of abuse across multiple application types
When an attack is identified, filtering rules are deployed inline in real time without disruption or human intervention.
Modular Filtering Architecture
Our system is built around modularity and performance, with layers including:
- Detection Layer → monitors and classifies traffic behavior
- XDP Filter Layer → enforces rules at the earliest point
- Control Plane → manages dynamic rules and visibility
- Mellanox NIC Offload → accelerates performance under load
This architecture allows us to respond fast, deploy updates live, and integrate easily with customer requirements.
Real-Time Metrics & Observability
We expose all filtering and detection metrics using standard observability tools, including:
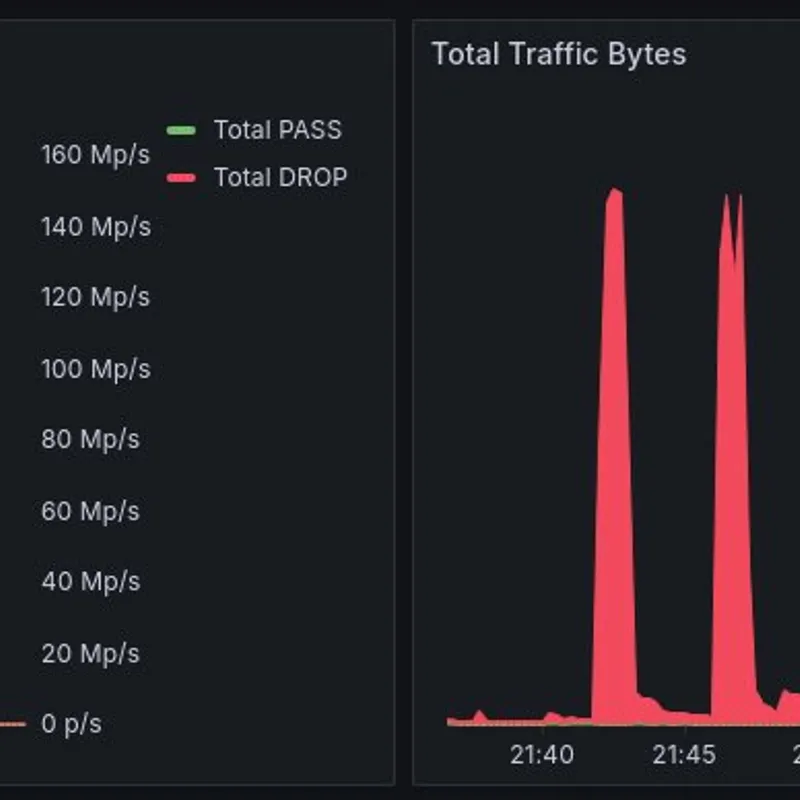
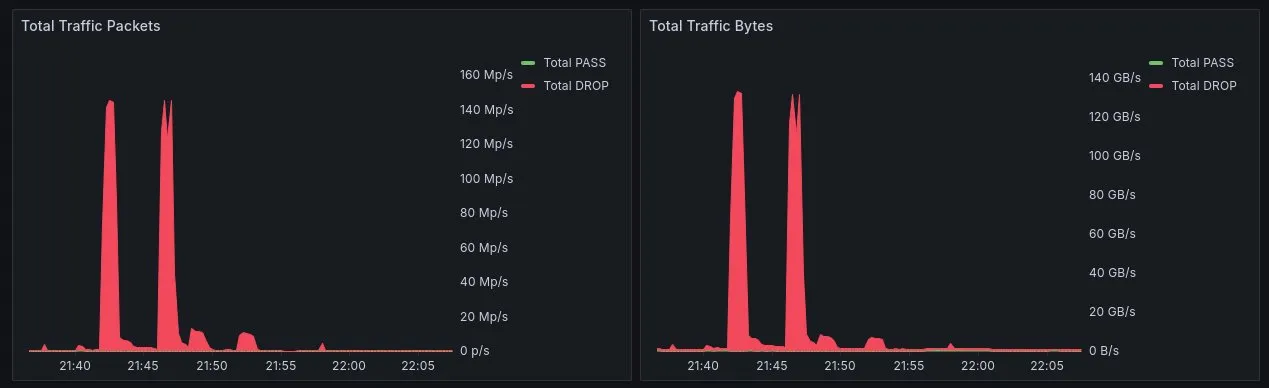
- PPS, BPS, drops, accepts, and match rates
- Geo, ASN, and endpoint-based summaries
- Alerting on behavioral triggers and thresholds
Our team and clients use these insights to stay ahead of threats and maintain transparency in how traffic is handled.
Why We Built It Ourselves
Most off-the-shelf DDoS protection systems come with trade-offs:
- Additional latency from redirection or challenge response
- Rigid or generic filtering logic
- Little control over detection or deployment behavior
We needed a solution that gave us full visibility, performance, and flexibility. So, we built it.
Now, we offer real-time, inline mitigation at the edge without complexity or compromise protecting:
- Real-time applications (VoIP, RDP, multiplayer gaming)
- API-first services and modern web stacks
- High-volume, low-latency systems with strict uptime needs
Curious to See It in Action?
We're proud of what we’ve built and we’re always improving it.
Whether you’re running HTTP, HTTPS, RDP, FiveM, Minecraft, or custom apps we’re ready to protect your traffic.
